Articles Details
Type: Computer Science Theory
Subject: Computer System Security
Background: Computer Network, Operating system.
Cryptography represents all the techniques used to protect information. Why cryptography is important? In a World of communication, the information is exchanged everyday. The cryptography is a part of our lives through use of Electric Card,password,online shopping and so on. In this article, we will see how the cryptography works through cryptography types, and cryptographic algorithms.
Introduction
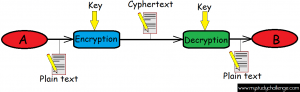
How does cryptography works? An Entity A want to send some data to another one B. Before sending the data, he will transform that data using a key in something apparently with no sense (Encryption). Then the B entity will recover the initial data using also a key (Decryption).
In the cryptography scenario, we have some important objects:
1.Two keys used for encryption and decryption
2.Two algorithms for encryption and decryption. C = enc(P) ; P = dec(C); C== Cipher Text(Encrypted text) and P == Plain text (Initial Text)
The Problem now is to know how is efficient an cryptography algorithm in respect of some kind of key. Auguste Kerchoff said
if the keys:
- are kept secret
- are managed only by trusted systems
- are of adequate length
then …
… it has no importance that the encryption and
decryption algorithms are kept secret
… on the countrary it is better to make the
algorithms public so that they can be widely
analysed and their possible weaknesses identified
Let’s discover the type of cryptography scenarios.
Cryptography type
Symmetric cryptography
In this scenario, we will use the same key for encryption and decryption. The key is shared between the A and B only.
This kind of cryptography is fast and can be compute on a large stream of data. Here we can use just symmetric algorithm like DES,3DES,IDEA,RC2,RC5,RC4 and AES. The disavantage of this type of cryptography is that we have to share in a sercure mode the private key between A and B.
Asymmetric cryptography
Here we use different keys for encryption and decryption. A key has two part(private key and public key). In this scenario, we use asymmetric algorithm like Dieffie-Helman,RSA,DSA, and El Gamal. This type of cryptography is used on small data amount (exchanging secret key) or digital signature.
Cryptographic Algorithm
We have two main class of cryptographic algorithm: block and stream
Block algorithms
Block algoritm are methods which encrypt or decrypt a specific size of data at the time(block data). So they divide the data in block of the same size and decrypt/encryt every block using a key.
Stream algorithms
Stream algorithm are algorithm which compute data one bit/byte at the time. So we have a key Stream use on one bit/byte at the time to encrypt/decrypt every bit/byte of the data.
The last think to say is that each cryptography algorithm has his own vulnerabilities but there is also a link between how difficult is to crack a cryptography algorithm and the length of the keys used.
Conclusion
In this article, we’ve covered the cryptography concept looking at his different types and algorithms. The next time we will go further in the algorithms details.
thank you for your time