In computer science, Port Scanning is a technique which send request to a range of ports on a host connected to a network. The goal is know all the open ports and in this way use the vulnerabilities of the services running on these ports to perform an attack to the target host. This technique is not always used for attacking purpose, it can also be used to analyse host vulnerabilities.
There exist some tools to perform port scanning without high knowledge in Network. One of these is the free software nmap written by Gordon Lyon.
In this article, we will see how to perform two kinds of port scanning using nmap.
Install nmap
The first think to do is download nmap and install it on your computer. You can find it here
In this article I use nmap version 6.01 on Windows 7.
Important note: some of the operations described in this article are illegal and are liable to prosecution. The purpose of this article is to present nmap just for didactic purpose. The author of this article decline any responsibility for actions performed by the vistitors of this blog in violation of this policy.
This is the structure of the nmap command:
nmap [ Scan Type ] [ Options ] { target specification }
For this article we use scanme.nmap.org as target specification . Normally we have to use the IP address of the target host.
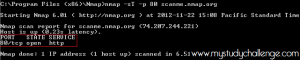
Scan on specific port
we want to perform a scan on the port 80 (Apache web server).
We will use this command:
nmap -sT -p 80 scanme.nmap.org
-sT means TCP connect() scan is use for TCP scan where we want try establish a connection.
-p 80 means port ranges in our case, one specified port: -p [port number]
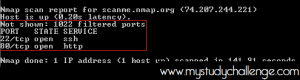
Scan on multiple ports
we want to perform a scan on the first 1024 ports.
We will use this command:
nmap -sT -p 1-1024 scanme.nmap.org
-p 1-1024 means port ranges in our case, from 1 to 1024: -p [first port number]-[last port number]
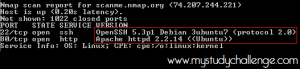
Identification of Services
A service is an application running(listening) on a port. Example Apache run on port 80.
we want to perform a scan that also identify what services are listening on ports of the target host.
we will use this command:
nmap -sV -p 1-1024 scanme.nmap.org
-sV SERVICE/VERSION DETECTION
Protect yourself
The best way to protect a computer from a port scanning is the use of a Firewall because he can filter incoming connections and block them.
For futher knowledge go to the nmap documentation


😉 😉 😉
Really informative article post.Really thank you!
TCP connect scan is the default TCP scan type when SYN scan is not an option. This is the case when a user does not have raw packet privileges. Instead of writing raw packets as most other scan types do, Nmap asks the underlying operating system to establish a connection with the target machine and port by issuing the